- 22 Mar 2021
- 4
- 3
I had Evolution X Android 11 on lavender. Some encryption problems happened while updating to a newer version. I then flashed the stock MIUI 12. More encryption problems happened.
My internal storage shows up as 0MB on TWRP. Many folders in TWRP's file manager appear as empty, except the microsd card's folder. TWRP accepts the password and shows that the data is being decrypted, but I get an error of "Unable to mount storage"
I then installed a custom modded version of TWRP which is designed for Xiaomi encryption issues. It seems to have the same thing. It looks like it's accepting the password, although the message screen moves too quickly for me to be able to read it. However, the "Unable to mount storage" error remains.
I imaged the userdata partition to my PC. (mmcblk0p66.img) Then I used a script to grab some ***** footer/magic flags data from this image.
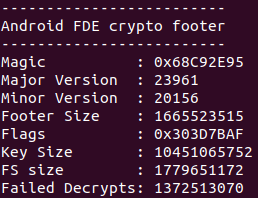
However, I am confused on which commands I should run to restore my data using this information. I was following these two guides: Link 1 ... Link 2
I was supposed to convert the flags to little endian and search for that within HxD inside my mmcblk0p66.img file. But I'm not sure how exactly to do this. What I have done within HxD might be wrong, as I'm not seeing any information that I can understand related to these byte patterns.
Does anybody know a way? Is it possible to restore my data using some other method as well?
Thanks!
My internal storage shows up as 0MB on TWRP. Many folders in TWRP's file manager appear as empty, except the microsd card's folder. TWRP accepts the password and shows that the data is being decrypted, but I get an error of "Unable to mount storage"
I then installed a custom modded version of TWRP which is designed for Xiaomi encryption issues. It seems to have the same thing. It looks like it's accepting the password, although the message screen moves too quickly for me to be able to read it. However, the "Unable to mount storage" error remains.
I imaged the userdata partition to my PC. (mmcblk0p66.img) Then I used a script to grab some ***** footer/magic flags data from this image.
However, I am confused on which commands I should run to restore my data using this information. I was following these two guides: Link 1 ... Link 2
I was supposed to convert the flags to little endian and search for that within HxD inside my mmcblk0p66.img file. But I'm not sure how exactly to do this. What I have done within HxD might be wrong, as I'm not seeing any information that I can understand related to these byte patterns.
Does anybody know a way? Is it possible to restore my data using some other method as well?
Thanks!